A company told one man to pack up his desk, then realized he still held the keys to everything.
Imagine this: You manage the core routers that move traffic across the country. You get paged at three in the morning when anything hiccups. You live inside this network more than you live inside your own living room.
Then one day, the boss’ boss calls you into an office. You hear the classic script about “downsizing” and “tough decisions.” You sign the papers. Those same papers say you no longer work there and cannot do any work for them.
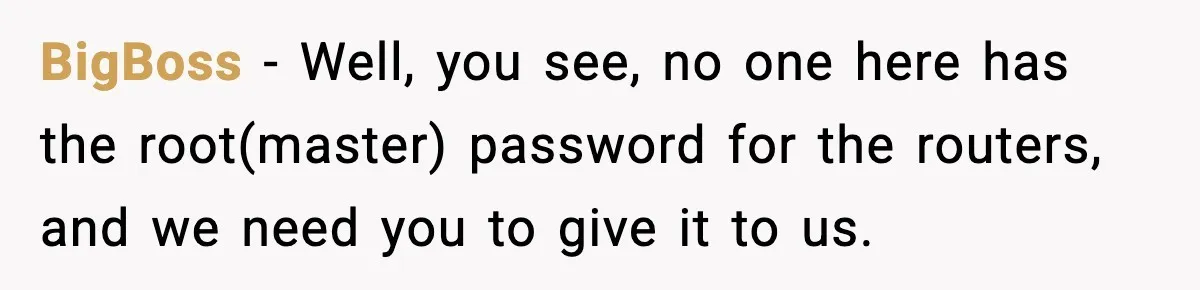
You go to a farewell lunch, swap a few dark jokes about servers, then head home. An hour later the phone rings. The same boss now needs the one thing nobody else has. The master router password.
And your dad’s answer turns the whole thing into a corporate fairy tale with teeth.
Now, read the full story:






















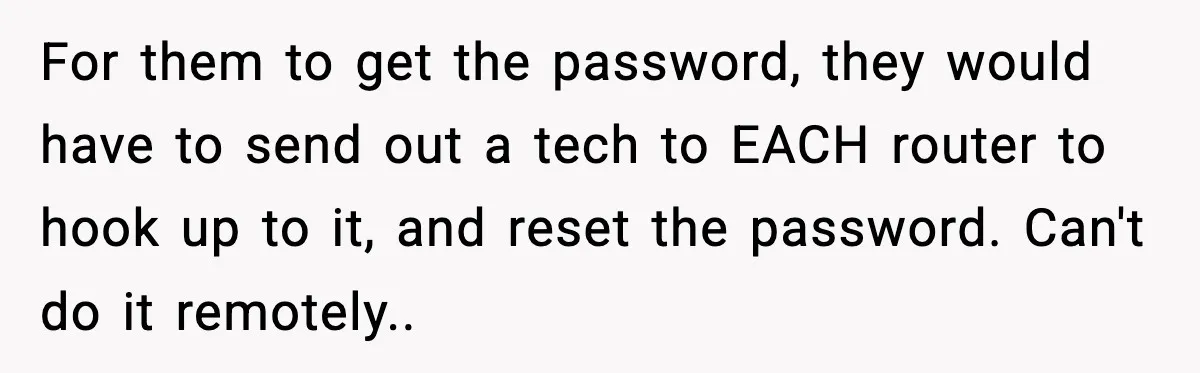





I love how quietly cold this is. No sabotage. No screaming. No drama in the office parking lot. Just a man who leaves, sits down at home, and remembers that every router listens only to him.
You feel his hurt in that shorter tone on the phone. He just lost his job. He lost the sleep and the 3am pages too. Then management suddenly remembers his worth, but only because they need something.
His consulting answer feels less like revenge and more like balance. You ended the relationship. You wrote that I cannot work for you. So, if you want work now, you treat it like work and pay for it.
This kind of story hits every burned-out IT worker right in the ribs. This quiet power shift shows up in a lot of modern workplaces.
At first glance, this looks like a clean little revenge story. You fire the network guy, then scramble when you realize you never documented the passwords.
Underneath, the story reveals a pattern that security experts worry about every day. Companies rush layoffs and forget the “boring” part: knowledge transfer and access control.
Terranova Security explains that improper offboarding opens big security holes. They note that 76 percent of IT professionals see offboarding as a significant security threat and warn that organizations must treat departures as security events, not just HR paperwork.
Beyond Identity and related research show how serious this gets in real numbers. One summary reports that 89 percent of former employees still hold access to at least one application from a past employer.
Security Magazine adds that almost a third of companies admit former staff accessed SaaS data after leaving.
So the dad’s story does not live in some fantasy IT world. It sits inside a very real pattern. Companies move fast, skip documentation, and leave one person with all the keys.
From a risk point of view, that single point of failure creates two problems. If that person leaves and stays friendly, you still depend on their goodwill. If that person leaves angry, you may face a locked door.
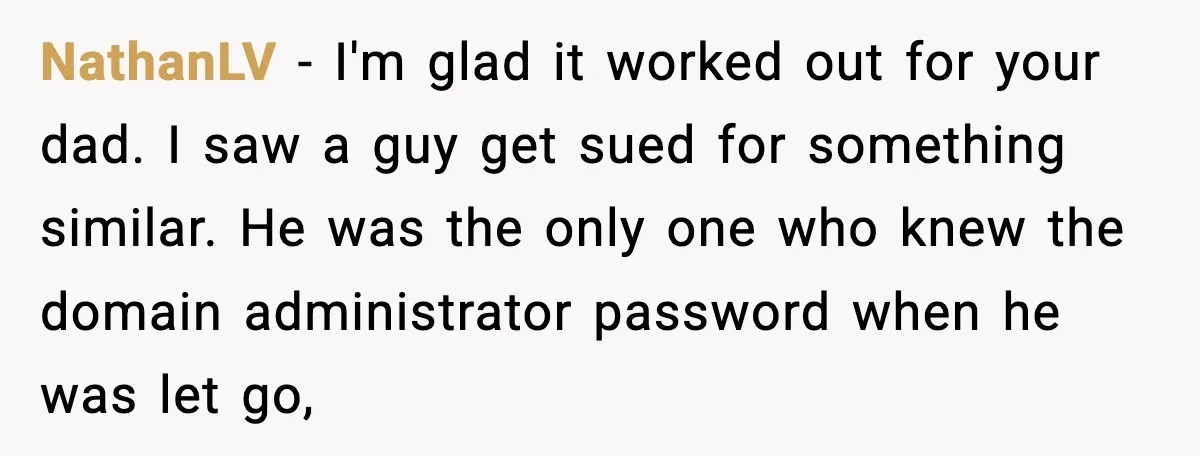
The Terry Childs case in San Francisco shows an extreme version. He refused to give admin passwords for the city’s network, kept staff locked out for 12 days, and received a four-year prison sentence for network tampering.
That case sits in a very different legal territory than this dad. Childs controlled the system while still employed and defied orders. The dad simply left, signed paperwork forbidding further work, then declined unpaid help. Big difference.
So what are the lessons here, beyond “do not fire the only network admin”?
First, leadership must treat IT offboarding as a core security process. Gusto’s offboarding guide tells managers to revoke system access and change shared passwords on the employee’s last day, because any delay invites trouble. That includes root credentials, router access, cloud consoles, everything.
Second, teams need shared knowledge. If one person “owns” all the scripts, all the diagrams, all the passwords, then leadership already built a time bomb. Good engineering culture spreads critical knowledge across people and documentation.
Third, IT workers can learn from the dad’s calm approach. He did not break anything. He did not threaten. He simply priced his labor once they asked for it again. That protects him ethically and legally.
Finally, this story reminds everyone that respect matters long before the last day. When companies treat skilled staff as replaceable, they underestimate the invisible work that holds everything together. You do not see the value of the 3am pager until you sit awake in your office with no password and a silent network.
The dad’s laughter years later comes from that moment of sudden clarity. They saw his value only after they signed him away.
Check out how the community responded:
Some readers joked about the classic “this happened at my dad’s work” vibe and timing details.


Others dragged corporate logic for firing the one person who runs the backbone.



Some users brought up legal and ethical angles from similar real cases.


A few people zoomed out and talked about career strategy and not burning bridges.


Others focused on writing style quirks, acronyms, and petty corporate chaos.




This story feels funny on the surface, but it lands like a cautionary tale. You watch a company treat a critical engineer as disposable, then scramble when reality pushes back.
The dad did not break their systems. He did not take revenge in secret. He simply asked them to respect his time once they wanted his expertise again. Meanwhile, the company paid for years of poor documentation and lazy offboarding.
In a healthier setup, no single person would hold every root password. The team would document, rotate credentials, and close access properly on the last day. They would still miss him, but they would not need to beg for passwords an hour later.
So maybe the real moral sits here. If a business depends on one person and fires that person without a plan, that is not clever cost cutting. That is gambling with the entire operation.
What would you do if you were in the dad’s position? Would you give the password for free, or would you send your consulting rate too?












