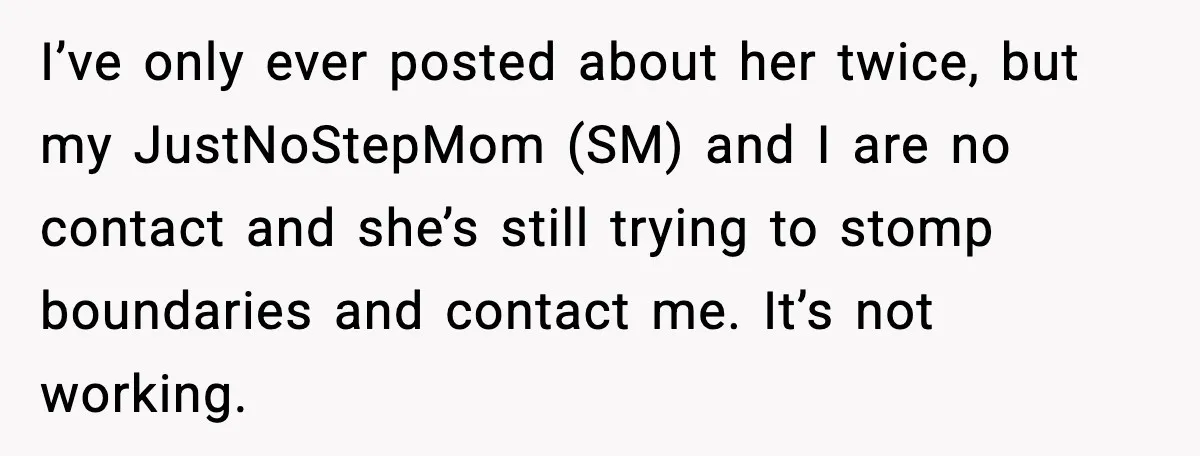
Sometimes the smallest protections bring the biggest relief.
For people dealing with boundary-stomping relatives, peace often comes in tiny victories. A blocked number. A locked door. A rule that finally gets respected.
For one pregnant woman, that victory came from something surprisingly simple. A password.
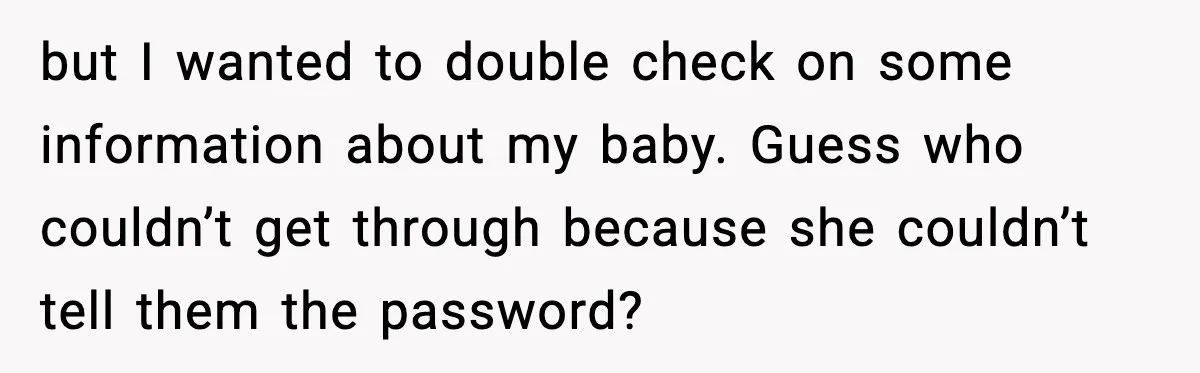
After years of no contact with her stepmother, she had learned the hard way that silence does not always mean safety. Even medical spaces were not off-limits to manipulation.
So she took precautions. She password-protected her OB records, double-checked permissions, and made sure only two people could access anything related to her pregnancy.
It felt like overkill. Until it wasn’t.
When her stepmother tried to impersonate her over the phone to access information about her baby, the system worked exactly as designed.
The call went nowhere. And for once, the boundary held.
The community’s reaction ranged from celebration to concern to very creative password suggestions.
Now, read the full story:








 This is one of those moments that feels both validating and unsettling. Validating because the system did exactly what it was supposed to do. The preparation paid off. The boundary held.
This is one of those moments that feels both validating and unsettling. Validating because the system did exactly what it was supposed to do. The preparation paid off. The boundary held.
Unsettling because someone felt entitled enough to impersonate a pregnant woman to access medical information.
That is not curiosity. That is control.
The relief in this story is quiet but powerful. No confrontation. No explosion. Just a calm notification that the attempt failed.
Sometimes safety looks like drama. Sometimes it looks like a receptionist calmly saying no.
And sometimes, it looks like a password doing its job.
This story highlights a critical issue that mental health professionals frequently see in cases involving estranged family members.
Boundary violation does not stop just because contact ends.
According to research on relational control, individuals who previously had access to someone’s personal information often struggle to accept the loss of that access.
Medical settings are a common target.
Healthcare providers are seen as authority figures who might be manipulated, especially when impersonation is involved. Studies on identity misuse show that family members account for a significant portion of non-financial impersonation attempts.
What makes this case especially concerning is the impersonation itself.
Pretending to be someone else in a medical context is not just unethical. In many jurisdictions, it can be considered fraud or unlawful access to protected health information.
HIPAA guidelines in the U.S. explicitly require safeguards against unauthorized disclosure, including verbal verification processes like passwords.
From a psychological perspective, the stepmother’s behavior fits a pattern known as entitlement-based intrusion.
This occurs when someone believes their emotional connection grants them ongoing access, regardless of consent.
In these cases, boundaries are interpreted as challenges rather than limits.
The password system worked because it removed emotional leverage. No guilt. No explanation. No argument.
Just a rule.
Experts consistently recommend this type of neutral barrier for people dealing with persistent boundary violators.
It shifts enforcement away from the individual and onto a system, reducing emotional strain.
Another important takeaway is redundancy.
The OP did not rely on a single safeguard. She confirmed access permissions multiple times and limited approved contacts.
This aligns with best practices in trauma-informed care, where layered protections reduce anxiety and improve feelings of safety. Community members also raised an important point about password choice.
Using dates tied to life events can be memorable but potentially guessable. Experts recommend nonsensical phrases or emotionally neutral strings when possible.
That said, the key success here was not the password itself. It was the decision to protect information proactively. This story demonstrates that boundaries are not just emotional tools. They can be procedural, quiet, and incredibly effective.
Check out how the community responded:
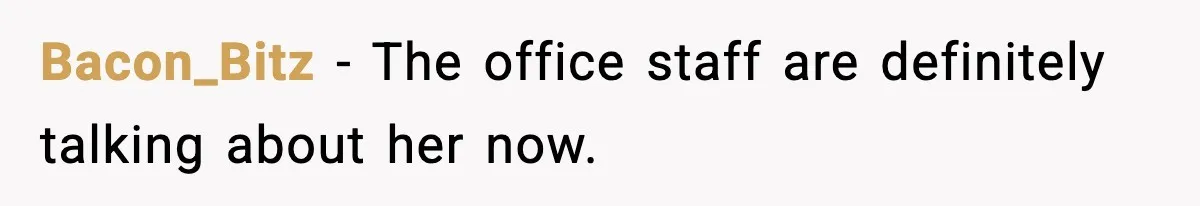
Many commenters celebrated the system working as intended.


Others focused on improving password security.


![Woman Locks Down Medical Info, Step-Mom’s Scheme Instantly Fails [Reddit User] - Change it if she ever learns the date.](https://dailyhighlight.com/wp-content/uploads/2026/02/wp-editor-1770477804878-3.webp)
Some raised legal and ethical concerns.

![Woman Locks Down Medical Info, Step-Mom’s Scheme Instantly Fails [Reddit User] - This is deeply unsettling behavior.](https://dailyhighlight.com/wp-content/uploads/2026/02/wp-editor-1770477851373-2.webp)
![Woman Locks Down Medical Info, Step-Mom’s Scheme Instantly Fails [Reddit User] - Why does she even want this info?](https://dailyhighlight.com/wp-content/uploads/2026/02/wp-editor-1770477854768-3.webp)
This story is not loud. There is no shouting. No confrontation. No dramatic fallout.
And that might be why it feels so powerful. The OP did not have to defend herself. She did not have to explain. She did not have to relive old wounds.
A boundary was set. A system enforced it. That is often the safest outcome when dealing with someone who refuses to respect limits.
It also serves as a reminder that medical privacy matters deeply, especially during vulnerable moments like pregnancy.
This wasn’t paranoia. It was preparation. And it worked.
So what do you think? Should medical offices require stronger verification by default? And have you ever had to rely on a quiet system, rather than confrontation, to protect your boundaries?





















