A slick-talking Cadillac salesman crowned himself the showroom’s secret tech king, slipping in USB drives loaded with forbidden tools, snatching permanent admin rights, and turning a shared desk into his private fortress. Everyone else fumed while the real sysadmin begged management for help and got nothing but shrugs and “handle your own mess” replies.
Finally pushed to the brink, the overlooked IT pro snapped. With zero backup from the top brass, he quietly built an iron-clad digital cage, rolled it out overnight, and watched the self-proclaimed computer genius crumble when his tricks suddenly stopped working. The entire sales floor felt the squeeze and the culprit wandered around useless.
IT pro locks down dealership PCs after management refuses to stop a rule-breaking salesman.








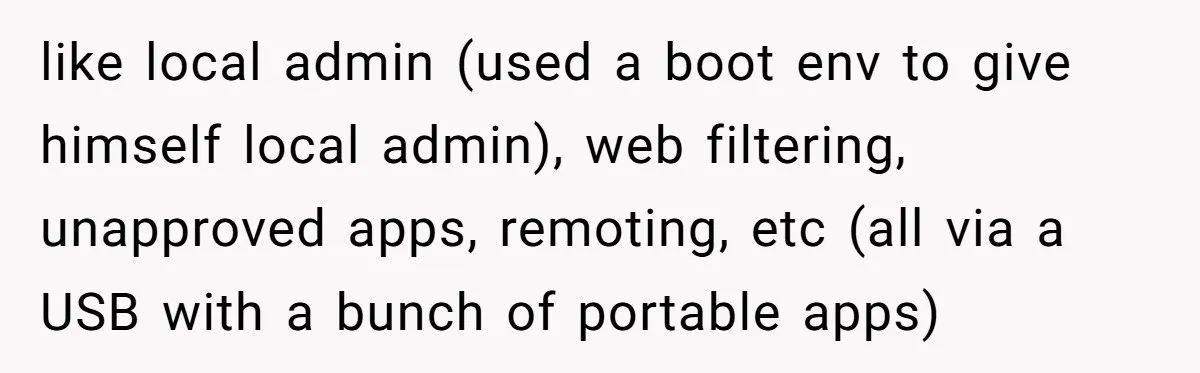







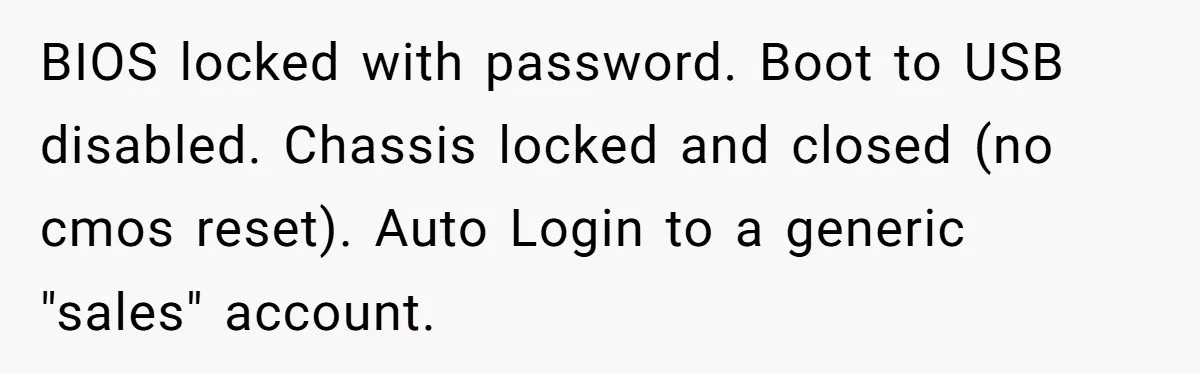
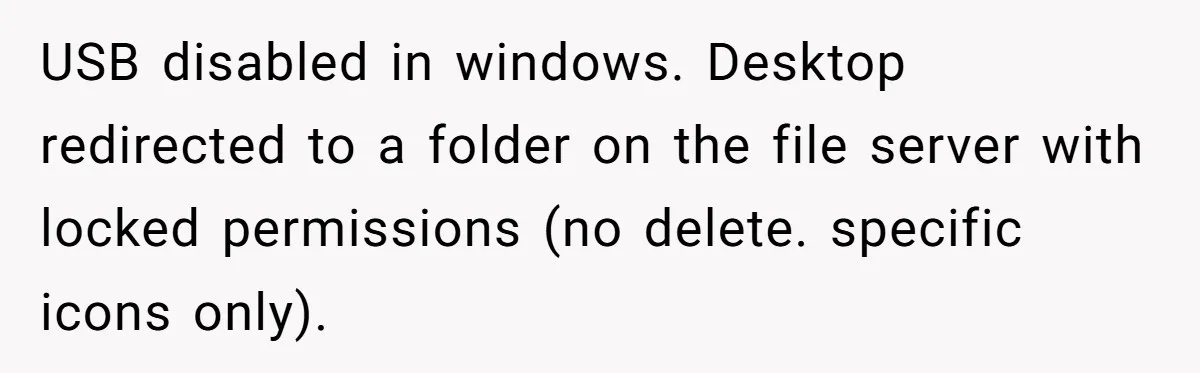

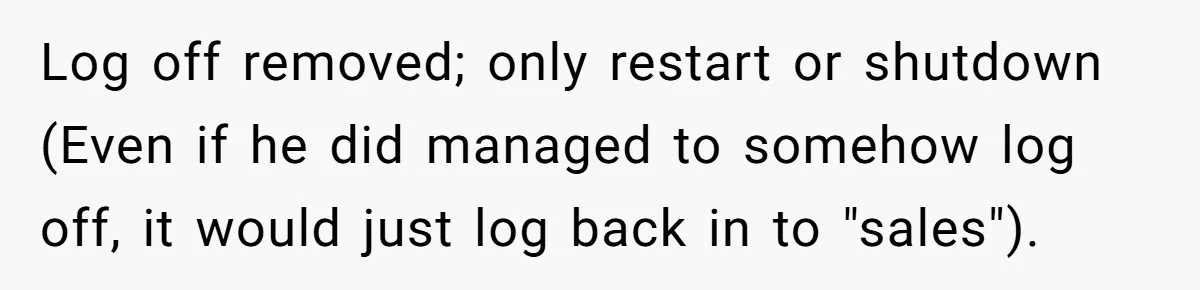











At the heart of the story, our OP wasn’t dealing with a clueless grandma clicking phishing links; he was up against a self-taught salesman who knew just enough to be a walking security violation. Management’s response “That’s an IT problem” basically gave him a blank check to go full fortress mode.
On one side, you’ve got the salesman who probably felt like he was just “optimized” his workflow. On the other, you’ve got literally every other salesperson who couldn’t use the shared desk, plus a sysadmin whose phone wouldn’t stop blowing up.
When leadership shrugs and says “not my circus, not my monkeys,” the ringmaster has to take drastic measures, or watch the circus burn.
This story is a textbook example of why organizations lock everything down in the first place. Verizon’s 2024 Data Breach Investigations Report found that the human element – such as errors, privilege misuse, and social engineering – plays a role in 68% of breaches, with stolen credentials involved in 49% of cases.
One overconfident user with a USB stick can become the human element that costs millions. In a 2019 CSO Online article, security expert Roger Grimes warned: “Overly permissive permissions may or may not be the fourth biggest cybersecurity risk, but given the headlines about permissions mistakes exposing huge amounts of data, it sure seems to be the case.”
He was discussing the dangers of incorrect access controls in general, but he might as well have been narrating this dealership drama. The salesman wasn’t malicious (probably), but his “a little knowledge is dangerous” attitude created exactly the kind of risk Grimes warns about. The sysadmin’s nuclear lockdown wasn’t personal; it was survival.
Healthy workplaces draw clear lines: IT sets technical policy, management enforces behavioral policy. When those lines blur, everyone suffers, except the one guy with the USB, until someone finally yeets that USB into the sun (metaphorically).
The real fix? Leadership training that treats security policy like any other company rule, because “it’s just computers” is how ransomware brunch gets served.
Here’s the input from the Reddit crowd:
Some people say the salesman’s actions were a clear security violation and management dropped the ball by not enforcing policy.
![Car Salesman Hijacks Dealership Computers Until IT Admin Delivers Company-Wide Lockdown Revenge [Reddit User] − "This isn't a management problem when it involves computers." I respectfully disagree with your managers.](https://dailyhighlight.com/wp-content/uploads/2025/12/wp-editor-1765254725245-1.webp)






Some people explain that overly strict restrictions exist because of users exactly like this salesman.




Some people share their own horror stories of clueless or rogue users breaking everything.






Some people are simply satisfied that the rogue user finally got what was coming to him.



At the end of the day, one IT pro turned “not my job” into “watch me make it my job” and delivered karma so cold it needed a jacket. Do you think the full-sales-floor lockdown was genius justice, or did it punish the innocent along with the guilty? Would you have gone nuclear, or tried one more polite email to management? Drop your verdict in the comments!





















