Companies invest in phishing awareness to shield data, training staff to spot urgency, odd links, or sender mismatches. Tests reinforce vigilance without real risk.
One worker failed a drill using job-required social media, enduring extra sessions. Soon, the IT director flagged a quiz deadline via attachment. Hover previews raised flags, prompting reports.
Clarifications arrived, yet patterns persisted. Does the caution loop endlessly? Scroll down for the high-importance chain and Redditors’ rule ideas.
One cautious employee turned mandatory phishing training into an endless report loop on the IT director’s own emails






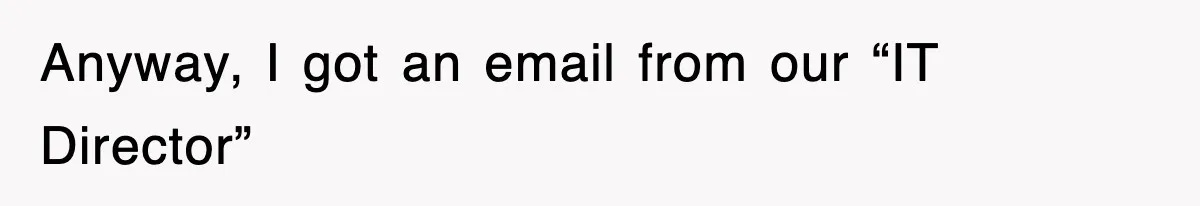






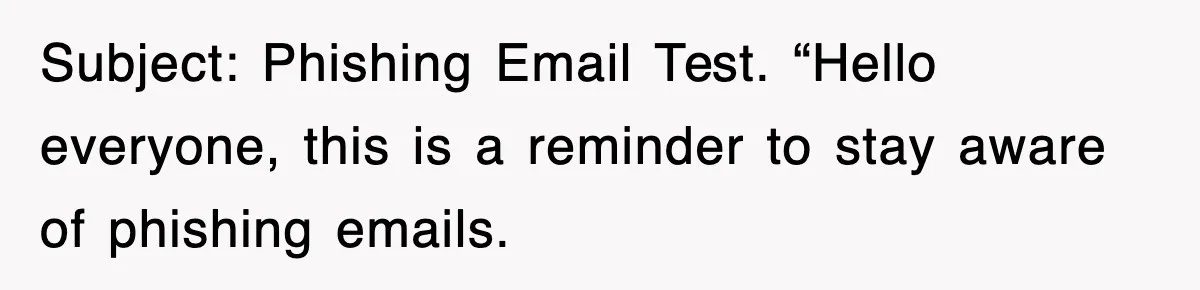






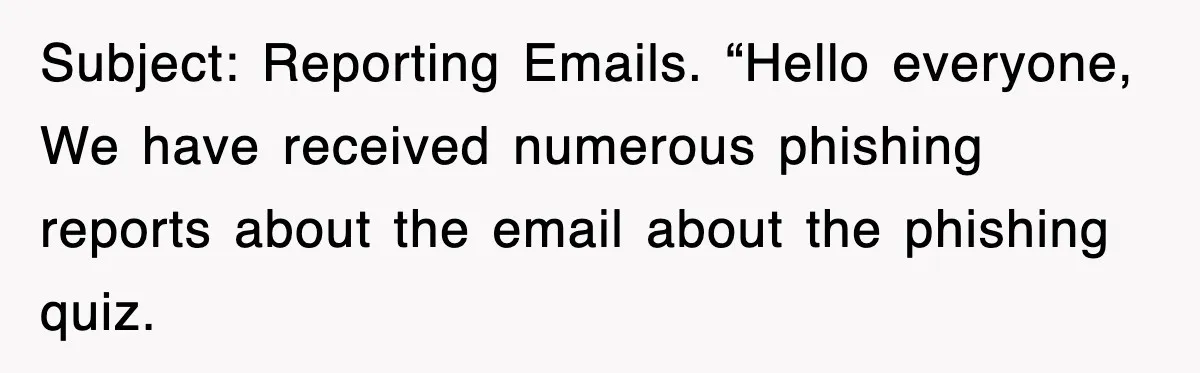






Phishing awareness campaigns often use simulated attacks to test employee vigilance, but they can accidentally mimic “real” threats. That confusion leads to repeated reporting and frustration.
According to the 2023 Verizon Data Breach Investigations Report, analysts reviewed 16,312 incidents, including 5,199 confirmed data breaches, and found that social engineering remained one of the most common tactics used by attackers.
The IT director’s emails, marked ” high importance” and urging immediate action, show common pitfalls. Time pressure and urgency are classic red flags taught in phishing training.
This irony weakens trust. Employees like the original poster apply what they learned correctly. Yet they’re told they’re wrong through clarifications that sound like real phishing messages.
For example: “Please note, any email from [address] is not phishing.” That kind of statement mirrors actual scam tactics.
The repeated cycle of reporting and rebuttal over two months shows poor program calibration. Proofpoint’s 2024 State of the Phish report noted that unclear simulations often cause confusion and false reports, wasting resources and breeding cynicism.
In this case, the director’s failure to pre-announce tests and lack of distinct branding, like “Simulation” in the subject line, broke best practices from NIST. NIST’s Cybersecurity Framework recommends transparent debriefs that reinforce learning, not defensive confusion.
The original poster’s persistence was ideal. They followed protocol perfectly by reporting suspicious messages. SANS Institute guidelines say employees “should” report any suspicious email, even internal ones.
According to IBM’s 2022 report, spoofing internal domains is a common feature of advanced phishing campaigns. Research from KnowBe4 also suggests that positive reinforcement, such as rewarding accurate reports, is more effective than punishment in reducing phishing clicks.
To fix this, IT leaders should review the simulation balance between realism and confusion. They should use clear sender signatures like “[email protected]” and share analytics openly afterward.
If employees feel fatigued, anonymous feedback channels can help. That aligns with OSHA’s stress mitigation policies under the General Duty Clause.
Ultimately, a strong cybersecurity culture grows through respect and iteration. Employees who report are assets, not annoyances. Celebrating them builds vigilance without burnout.
Here’s the feedback from the Reddit community:
Redditors laughed about accidentally flagging real cybersecurity drills as scams

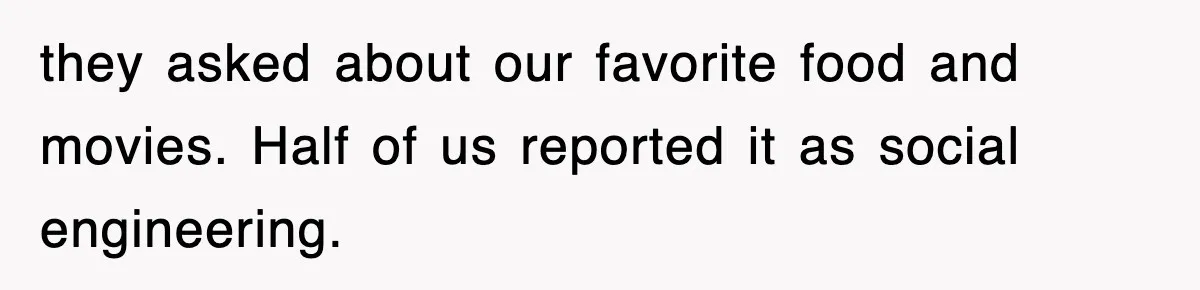






Users roasted the “my email is safe” line as classic phisher behavior



Commenters joked about auto-flagging every IT director email out of caution




Redditors mocked phishing tests that outsmart their own creators










One deadline became a delightful do-loop, proving training works, maybe too well. Would you keep reporting or request clearer headers? Drop your inbox insurrection tales below!





















